httpd
httpd是Apache超文本传输协议(HTTP)服务器的主程序,httpd是最能代表apache的ASF的开源产品,也是目前世界上使用最多的web服务器,下面我们来说说httpd的基础配置。
web服务器的占比
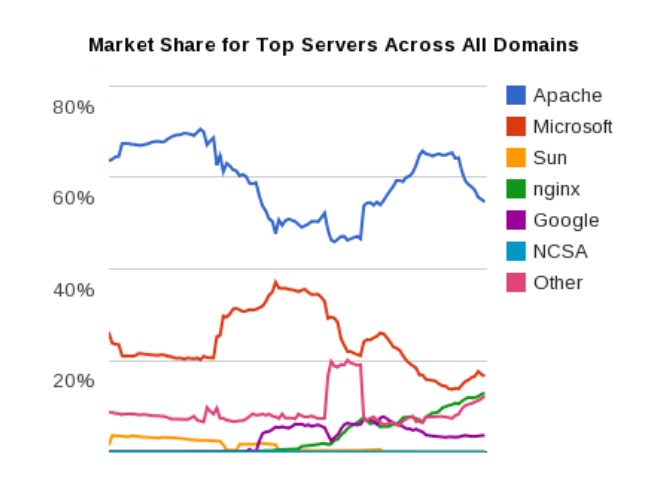
http
一次完整的http请求处理过程:
-(1)建立或处理连接:接受请求或拒绝请求;
-(2)接受请求:接受来自于网络的主机请求报文中对某特定资源的一次请求的过程
-(3)处理请求:对请求报文进行解析,获取客户端请求的资源及请求方法等相关信息
-(4)访问资源:获取请求报文中请求的资源
-(5)构建响应报文
-(6)发送响应报文
-(7)记录日志
接受请求的模型:
1 | 并发访问的响应模型: |
2 | 单进程i/o模型:启动一个进程处理用户请求;这意味着,一次只能处理一个请求,多个请求被串行响应; |
3 | 多进程i/o模型:并行启动多个进程,每个进程响应一个请求 |
4 | 复用的i/o模型:一个进程响应n个请求 |
5 | 多进程模式:一个进程响应m个请求,一个线程处理一个请求 |
6 | 事件驱动(event-driven): 一个进程响应m个请求 |
7 | 复用的多进程i/o结构:启动多个(m)个进程,每个进程生成(n)个线程 |
8 | 响应的请求的数量:m*n |
httpd
httpd的特性
1 | 高度模块化:core+modules |
2 | DSO: dynamic shared object |
3 | MPM: Multipath processing Modules(多路处理模块) |
4 | prefork:多进程模型,每个进程响应一个请求; |
5 | 一个主进程:负责生成子进程集回收子进程;负责创建套接字;负责接受请求,并将其派发给某子进程进行处理; |
6 | n个子进程:每个子进程处理一个请求; |
7 | 工作模式:会预先生成n个空闲进程,随时等待用于响应用户请求;最大空闲和最小空闲 |
8 | |
9 | worker:多进程多线程模型,每线程处理一个用户请求; |
10 | 一个主进程:负责生成子进程;负责创建套接字;负责接受请求,并将其派发给某子进程进行处理; |
11 | 多个子进程:每个子进程负责生成多个线程; |
12 | 每个线程:负责响应用户请求 |
13 | 并发响应数量:m*n |
14 | m: 子进程数量 |
15 | n: 每个子进程所能创建的最大线程数量 |
16 | |
17 | event: 事件驱动模型,多进程模型,每个进程响应多个请求; |
18 | 一个主进程:负责生成子进程;负责创建套接字;负责接受请求,并将其派发给某子进程进行处理; |
19 | 子进程:基于事件驱动机制直接响应多个请求 |
20 | httpd-2.2:仍为测试使用模型 |
21 | httpd-2.4:event 可生产环境中使用 |
httpd 目录结构
采用yum安装的httpd的结构,centos6默认安装httpd-2.2,centos7默认安装httpd-2.4
centos6 httpd-2.2
1 | 程序环境: |
2 | 配置文件: |
3 | /etc/httpd/conf/httpd.conf |
4 | /etc/httpd/conf.d/*.conf |
5 | 服务脚本: |
6 | /etc/rc.d/init.d/httpd |
7 | 脚本配置文件:/etc/syscofig/httpd |
8 | 主程序文件: |
9 | /usr/sbin/httpd |
10 | /usr/sbin/httpd.event |
11 | /usr/sbin/httpd.worker |
12 | 日志文件: |
13 | /var/log/httpd: |
14 | access.log:访问日志 |
15 | error.log:错误日志 |
16 | 站点文档: |
17 | /var/www/html |
18 | 模块文件路径: |
19 | /usr/lib64/httpd/modules |
centos7 httpd-2.4
1 | 程序环境: |
2 | 配置文件: |
3 | /etc/httpd/conf/httpd.conf |
4 | /etc/httpd/conf.d/*.conf |
5 | 模块相关的配置文件:/etc/httpd/conf/modules.d/*.conf |
6 | systemd unit file: |
7 | /usr/lib/systemd/system/httpd.service |
8 | 主程序文件: |
9 | /usr/sbin/httpd |
10 | httpd-2.4支持MPM的动态切换 |
11 | 日志文件: |
12 | /var/log/httpd: |
13 | access.log:访问日志 |
14 | error.log:错误日志 |
15 | 站点文档: |
16 | /var/www/html |
17 | 模块文件路径: |
18 | /usr/lib64/httpd/modules |
httpd-2.2的常用配置
主配置文件:/etc/httpd/conf/httpd.conf
- Section 1: Global Environment
- Section 2: ‘Main’ server configuration
- Section 3: Virtual Hosts
主要分三段配置
修改监听的ip和port
Listen [IP:]PORT
- (1)省略ip表示0.0.0.0
- (2)Listen 指令可重复初夏多次
Listen 80
Listen 8080 - (3)修改监听socket,重启服务进程方可生效
持久连接
persistent connection: tcp连续建立后,每个资源获取完成后不全断开连接,而是继续等待其它资源请求的进行
如何断开?
- 数量限制
- 时间限制
副作用:对并发访问量较大的服务器,长连接机制会使得后续某些请求无法得到正常响应
折中方法:使用较短的持久连接时长,以及较少的请求数量
1 | KeepAlive ON|Off |
2 | KeepAliveTimeout 15 |
3 | MaxKeepAliveRequests 100 |
测试:
1 | telnet 10.211.55.24 80 |
2 | GET /index.html HTTP/1.1 |
3 | Host: 10.211.55.24 |
开启持久连接在请求完成后仍会保持连接,直到超时时间。
MPM
http-2.2不支持同时编译多个MPM模块,所以只能编译选定要使用的那个;CentOS 6的rpm包专门提供了三个应用程序文件,httpd,httpd.worker,httpd.event,分别用于实现不同MPM机制。
默认使用的为prefork的MPM模块
查看httpd程序的模块列表:
查看静态编译的模块:
#httpd -l
查看静态编译及动态编译的魔块:
#httpd -M
更换使用httpd程序,以支持其它的MPM机制:
/etc/sysconfig/httpd
HTTPD=/usr/sbin/httpd.{worker,event}
MPM 配置
1 | <IfModule prefork.c> |
2 | StartServers 8 #开始服务的进程数 |
3 | MinSpareServers 5 #最小空闲进程 |
4 | MaxSpareServers 20 #最大空闲进程 |
5 | ServerLimit 256 #服务限制最大进程数 |
6 | MaxClients 256 #允许启动的最大进程数 |
7 | MaxRequestsPerChild 4000 #每个进程最大响应的请求数 |
8 | </IfModule> |
9 | |
10 | <IfModule worker.c> |
11 | StartServers 4 #开始服务的进程数 |
12 | MaxClients 300 #允许启动的最大进程数 |
13 | MinSpareThreads 25 #最小空闲进程 |
14 | MaxSpareThreads 75 #最大空闲进程 |
15 | ThreadsPerChild 25 #每个进程最大的线程数 |
16 | MaxRequestsPerChild 0 |
17 | </IfModule> |
DSO
配置指定实现模块加载
LoadModule
模块文件路径可使用的相对路径
相对于ServerRoot (默认/etc/httpd)
定义Main’server的文档页面路径
DocumentRoot “”
文档路径映射:
DocumentRoot 指向的路径为URL路径的起始位置
相当于站点URL的根路径
FileSystem)/web/host1/index.html --> (URL) /index.html
站点访问控制
可基于两种机制指明对哪些资源进行何种访问控制
文件系统路径:
1 | <Directory ""> |
2 | ... |
3 | </Directory> |
4 | |
5 | <File ""> |
6 | ... |
7 | </File> |
8 | |
9 | <FileMatch "PATTERN"> |
10 | ... |
11 | </FileMatch> |
URL路径:
1 | <Location ""> |
2 | ... |
3 | </Location> |
4 | |
5 | <LocationMatch ''> |
6 | ... |
7 | </LocationMatch> |
<Directory>中定义源地址实现访问控制:
(1)Opotions
后跟1个或多个空白分隔符字符隔开的“选项”列表
Indexes:指明的url路径下不存在与定义的主页面资源相符的资源文件时,返回索引列表给用户
FollowSymLinks:允许跟踪符号链接文件所指向的源文件
None:
All:(2) AllowOverride
与访问控制相关的哪些指令可以放在.htaccess文件(每个目录下都可以有一个)中;
All
None(3) order和allow,deny
order:定义生效次序,写在后面的表示默认法则:
Allow from
Deny from
定义站点主页面
DirectoryIndex index.html idex.html.var
定义路径别名
DocumentRoot “/www/htdocs”
Alias /download/ ‘/rpm/pub/‘ 相对于documentroot下为路径/rpm/htdocs设置别名
设定默认字符集
AddDefaultCharset UTF-8
中文字符集:GBK GB2312 GB18030
日志设定
日志类型: 访问日志 和 错误日志
错误日志:
ErrorLog logs/error_log
LogLevel warn
Possible values include: debug info notice warn error crit alert emerg访问日志:
LogFormat “%h %l %u %t "%r" %>s %b "%{Referer}i" "%{User-Agent}i"“ combined
CustomLog logs/access_log combined%h:客户端日志
%l:Remote User,通常为一个减号(‘-’);
%u:Remote User (from auth;may be bogus if return status (%s) is 401);非为登录访问时,其为一个减号
%t:服务器收到请求的时间
%r:请求报文的首行;记录了此次请求的“方法”,“url”以及协议版本
%>s:响应状态码
%b:响应报文的大小,单位是字节;不包括响应报文的http首部
%{Referer}i:请求报文中的首部“referer的值;即从哪个页面中的超链接跳转至当前页面;
%{User-Agent}i:请求报文中的首部”User-Agent”的值;即发出请求的程序
基于用户的访问控制
认证质询:
www-authenticate:响应码为401,拒绝客户端请求,并说明要求客户端提供账号和密码认证:
authenticate: 客户端用户填入账号和密码后再次发送请求报文;认证通过时,则服务器发送响应的资源
认证方式有两种:
basic:明文
digest:消息摘要认证安全域:需要用户认证后才能访问的路径;应通过名称对其进行标识,以便告知用户认证的原因:
虚拟帐号:仅用于访问某服务时用到的认证标识
存储:
- 文本文件
- SQL数据库
- ldap目录存储
basic认证配置示例:
(1)定义安全域
1<Directory ''>2Options None3AllowOverride None4AuthType Basic5AuthName "string"6AuthUserFile "/PATH/TO/HTTPD_USER_PASSWD_FILE"7Require user username1 username28</Directory>允许账号文件中所有用户登录访问:
Require valid-user(2) 提供账号和密码存储(文本文件)
使用专门命令完成此类文件的创建及用户管理
htpasswd [opotion] /path/to/httpd_file username
- -c:自动创建此处指定的文件,因此,仅应该在此文件不存在时使用
- -m: md5加密
- -s: shah格式加密
- -D: 删除指定用户
另外:基于组账号进行认证
- (1)定义安全域
1<Directory "">2Options None3AllowOverride None4AuthType Basic5AuthName "string"6AuthUserFile "/PATH/TO/HTTPD_USER_PASSWD_FILE"7AuthGroupFile "/PATH/TO/HTTPD_GROUP_FILE"8Require group grpname1 grpname29</Directory> - (2)创建用户账号和组账号文件:
组文件:每一行定义一个组
GRP_NAME:username1 username2 …
虚拟主机
注意:一般虚拟主机不要与中心主机混用;因此,要使用虚拟主机,得先禁用‘main’主机;
禁用方法:注释中心主机的DocumentRoot指令即可
共有三种虚拟主机设置:
- 基于ip
- 基于port
- 基于fqdn
虚拟主机的配置方法:
1 | <VirtualHost IP:PORT> |
2 | ServerName FQDN |
3 | DocumentRoot "" |
4 | <VirtualHost> |
httpd-2.2 基于虚拟主机的配置需要 NameVirtualHost IP:PORT
status页面
LoadModule status_module modules/mod_status.so
1 | <Location /server-status> |
2 | SetHandler server-status |
3 | Order deny,allow |
4 | Deny from all |
5 | Allow from .example.com |
6 | </Location> |
敏感访问目录,做好访问控制
user/group
指定以哪个用户的身份运行httpd服务进程
User apache
Group apache
使用mod_deflate模块压缩页面优化传输速度
适用场景:
- (1)节约带宽,额外消耗CPU;同时,可能有些老的浏览器不支持
- (2)压缩适合于压缩的资源,例如文本文件
我们需要查看服务器是否加载了此模块
~]# httpd -M | grep deflate
deflate_module (shared)
SetOutputFilter DEFLATE
设置输出过滤器
#Restrict compression to these MIME type
AddOutputFilterByType DEFLATE text/plain
AddOutputFilterByType DEFLATE text/html
AddOutputFilterByType DEFLATE application/xhtml+xml
AddOutputFilterByType DEFLATE text/xml
AddOutputFilterByType DEFLATE application/xml
AddOutputFilterByType DEFLATE application/x-javascript
AddOutputFilterByType DEFLATE text/javascript
AddOutputFilterByType DEFLATE text/css
#Level of compression(Highest 9 - Lowest)
DeflateCompressionLevel 9
#Netscape 4.X has some problems
BrowserMatch ^Mozilla/4 gzip-only-text/html
我们来测试下压缩
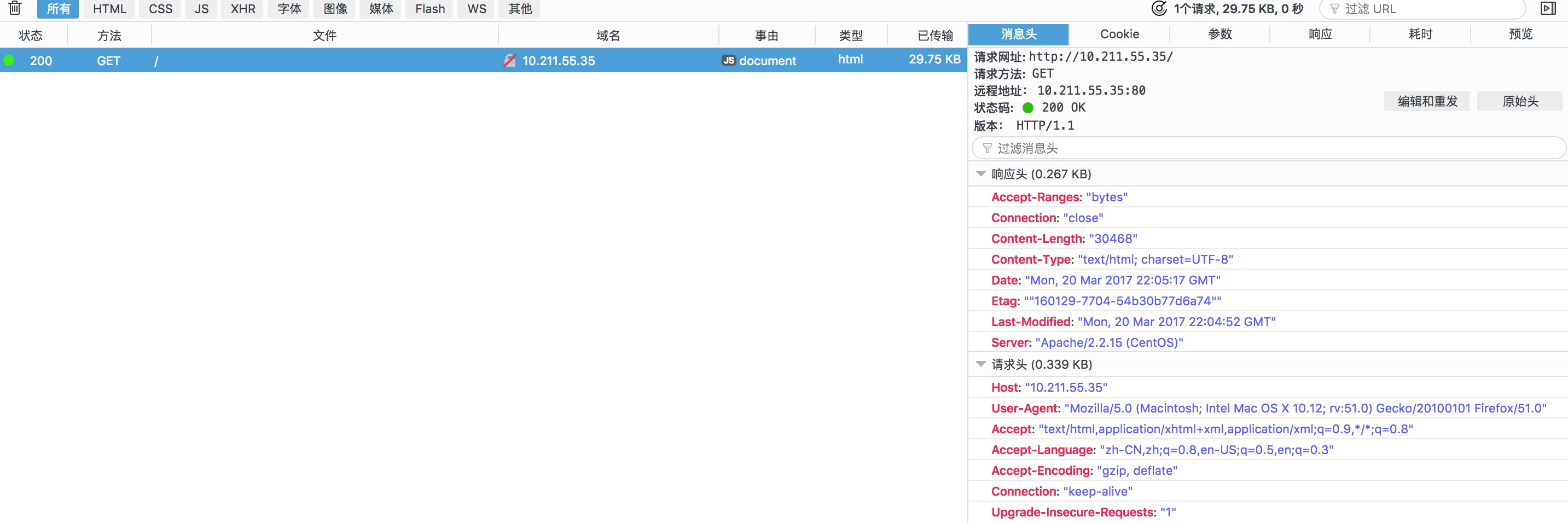
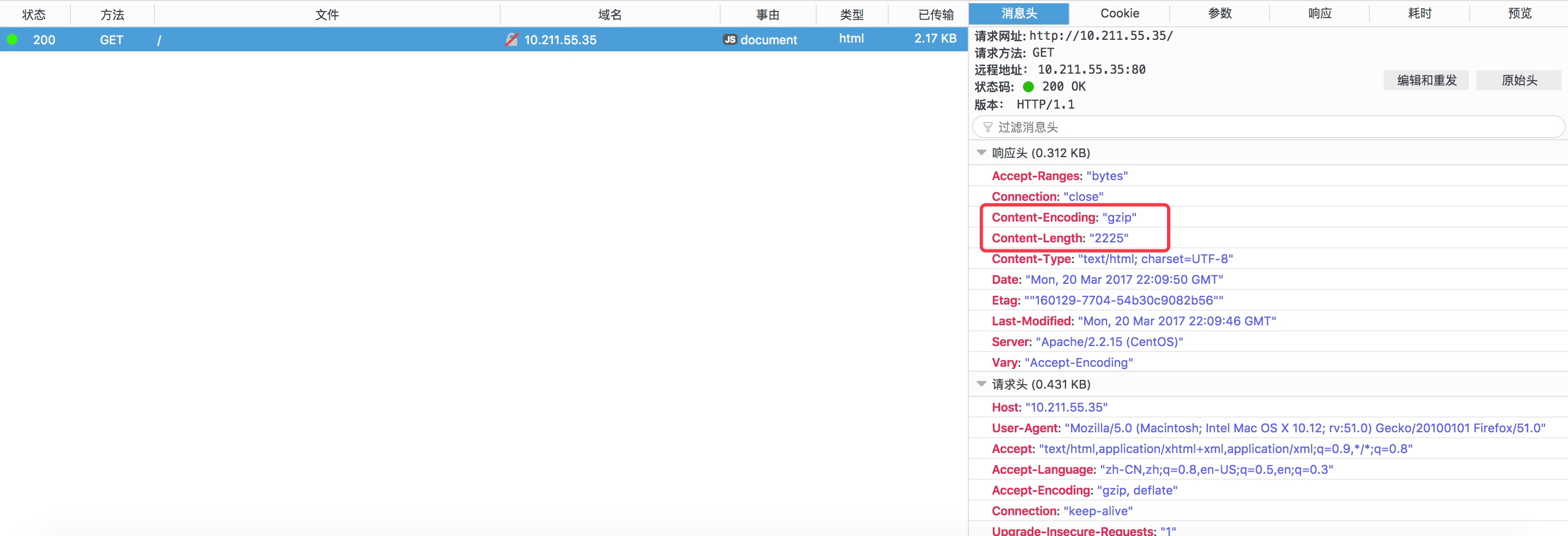
先制作个html页面,压缩一般都是针对文本界面进行压缩的:
1 | [root@www html]# cp /var/log/messages index.html |
2 | [root@www html]# chmod +r index.html |
3 | [root@www html]# vim /etc/httpd/conf/httpd.conf |
4 | SetOutputFilter DEFLATE |
5 | AddOutputFilterByType DEFLATE text/html |
6 | [root@www html]# service httpd restart |
https
SSL会话的简化过程
- (1)客户端发送可供选择的加密方式,并向服务器请求证书
- (2)服务器端发送证书以及选定的加密方式给客户端
- (3)客户端取得证书并进行证书验证:
(a) 验证证书的来源合法性;用CA的公钥解密证书上的数字签名
(b)验证证书的内容合法性,完整性验证
(c)检查证书的有效期限
(d)检查证书是否被吊销
(e)证书中拥有着的名字,与访问的目标主机要一致 - (4)客户端生成临时会话密钥(对称密钥),并使用服务器的公钥加密此数据发送给服务器,完成密钥交换
- (6)服务用此密钥加密用户请求的资源,响应给客户端
注意:ssl会话是基于ip地址创建;所以单ip的主机上,仅可以使用一个https虚拟主机
配置https支持https:
- (1)为服务器申请数字证书;
测试:通过私建CA发证书
(a)创建私有CA
(b)在服务器创建证书签署请求
(c)CA签证 - (2)配置httpd支持使用ssl,及使用的证书
#yum install -y mod_ssl
配置文件:/etc/httpd/conf.d/ssl.conf
DocumentRoot
ServerName
SSLCertificateFile
SSLCertificateKeyFile - (3)测试基于https访问相应的主机
#openssl s_client [-connect host:port][-cert filename][-CApath directory][-CAfile filename]
测试:
测试环境:http服务器与ca服务器都处于同一服务器
1、先建立私有ca
1 | [root@node2 ~]# cd /etc/pki/CA/ |
2 | [root@node2 CA]# ls |
3 | certs crl newcerts private |
4 | [root@node2 CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048) |
5 | Generating RSA private key, 2048 bit long modulus |
6 | .................................................................+++ |
7 | ..............................+++ |
8 | e is 65537 (0x10001) |
9 | [root@node2 CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3650 |
10 | You are about to be asked to enter information that will be incorporated |
11 | into your certificate request. |
12 | What you are about to enter is what is called a Distinguished Name or a DN. |
13 | There are quite a few fields but you can leave some blank |
14 | For some fields there will be a default value, |
15 | If you enter '.', the field will be left blank. |
16 | ----- |
17 | Country Name (2 letter code) [XX]:CN |
18 | State or Province Name (full name) []:ZJ |
19 | Locality Name (eg, city) [Default City]:HZ |
20 | Organization Name (eg, company) [Default Company Ltd]:JUSENE |
21 | Organizational Unit Name (eg, section) []:OPS |
22 | Common Name (eg, your name or your server's hostname) []:CA.JUSENE.COM |
23 | Email Address []:ADMIN@CA.COM |
24 | [root@node2 CA]# ls |
25 | cacert.pem certs crl newcerts private |
26 | [root@node2 CA]# touch serial index.txt |
27 | [root@node2 CA]# echo 01 > serial |
2、服务器请求签署证书
1 | [root@node2 ssl]# (umask 077;openssl genrsa -out httpd.key 2048) |
2 | Generating RSA private key, 2048 bit long modulus |
3 | ....................................+++ |
4 | .+++ |
5 | e is 65537 (0x10001) |
6 | [root@node2 ssl]# ls |
7 | httpd.key |
8 | [root@node2 ssl]# openssl req -new -key httpd.key -out httpd.csr -days 365 |
9 | You are about to be asked to enter information that will be incorporated |
10 | into your certificate request. |
11 | What you are about to enter is what is called a Distinguished Name or a DN. |
12 | There are quite a few fields but you can leave some blank |
13 | For some fields there will be a default value, |
14 | If you enter '.', the field will be left blank. |
15 | ----- |
16 | Country Name (2 letter code) [XX]:CN |
17 | State or Province Name (full name) []:ZJ |
18 | Locality Name (eg, city) [Default City]:HZ |
19 | Organization Name (eg, company) [Default Company Ltd]:JUSENE |
20 | Organizational Unit Name (eg, section) []:OPS |
21 | Common Name (eg, your name or your server's hostname) []:www.jusene.com |
22 | Email Address []:admin@jusene.com |
23 | |
24 | Please enter the following 'extra' attributes |
25 | to be sent with your certificate request |
26 | A challenge password []: |
27 | An optional company name []: |
28 | [root@node2 ssl]# openssl ca -in httpd.csr -out httpd.crt -days 365 |
29 | Using configuration from /etc/pki/tls/openssl.cnf |
30 | Check that the request matches the signature |
31 | Signature ok |
32 | Certificate Details: |
33 | Serial Number: 1 (0x1) |
34 | Validity |
35 | Not Before: Feb 26 18:53:32 2017 GMT |
36 | Not After : Feb 26 18:53:32 2018 GMT |
37 | Subject: |
38 | countryName = CN |
39 | stateOrProvinceName = ZJ |
40 | organizationName = JUSENE |
41 | organizationalUnitName = OPS |
42 | commonName = www.jusene.com |
43 | emailAddress = admin@jusene.com |
44 | X509v3 extensions: |
45 | X509v3 Basic Constraints: |
46 | CA:FALSE |
47 | Netscape Comment: |
48 | OpenSSL Generated Certificate |
49 | X509v3 Subject Key Identifier: |
50 | FC:CA:DE:D8:79:17:B3:12:16:50:FD:27:B2:76:7F:84:AE:F6:8F:65 |
51 | X509v3 Authority Key Identifier: |
52 | keyid:FD:CD:68:2D:2C:BF:71:2E:C7:91:AB:6F:60:20:29:65:2A:6F:82:88 |
53 | |
54 | Certificate is to be certified until Feb 26 18:53:32 2018 GMT (365 days) |
55 | Sign the certificate? [y/n]:y |
56 | |
57 | |
58 | 1 out of 1 certificate requests certified, commit? [y/n]y |
59 | Write out database with 1 new entries |
60 | Data Base Updated |
61 | [root@node2 ssl]# ls |
62 | httpd.crt httpd.csr httpd.key |
3、配置站点
1 | [root@node2 ssl]# yum install -y mod_ssl |
2 | [root@node2 ssl]# rpm -ql mod_ssl |
3 | /etc/httpd/conf.d/ssl.conf |
4 | /usr/lib64/httpd/modules/mod_ssl.so |
5 | /var/cache/mod_ssl |
6 | /var/cache/mod_ssl/scache.dir |
7 | /var/cache/mod_ssl/scache.pag |
8 | /var/cache/mod_ssl/scache.sem |
9 | [root@node2 ssl]# vi /etc/httpd/conf.d/ssl.conf |
10 | 修改虚拟主机的DocumentRoot ServerName |
11 | SSLCertificateFile /etc/httpd/ssl/httpd.crt |
12 | SSLCertificateKeyFile /etc/httpd/ssl/httpd.key |
13 | [root@node2 ssl]# httpd -t |
14 | [root@node2 ssl]# service httpd restart |
15 | [root@node2 ssl]# netstat -ntlp |
16 | Active Internet connections (only servers) |
17 | Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name |
18 | tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1664/sshd |
19 | tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 1751/master |
20 | tcp 0 0 :::80 :::* LISTEN 9254/httpd |
21 | tcp 0 0 :::22 :::* LISTEN 1664/sshd |
22 | tcp 0 0 ::1:25 :::* LISTEN 1751/master |
23 | tcp 0 0 :::443 :::* LISTEN 9254/httpd |
4、443端口启动,测试ssl功能
1 | 在远程主机上测试 |
2 | [root@www conf.d]# openssl s_client -connect www.jusene.com:443 |
3 | CONNECTED(00000003) |
4 | depth=0 C = CN, ST = ZJ, O = JUSENE, OU = OPS, CN = www.jusene.com, emailAddress = admin@jusene.com |
5 | verify error:num=20:unable to get local issuer certificate |
6 | verify return:1 |
7 | depth=0 C = CN, ST = ZJ, O = JUSENE, OU = OPS, CN = www.jusene.com, emailAddress = admin@jusene.com |
8 | verify error:num=27:certificate not trusted |
9 | verify return:1 |
10 | depth=0 C = CN, ST = ZJ, O = JUSENE, OU = OPS, CN = www.jusene.com, emailAddress = admin@jusene.com |
11 | verify error:num=21:unable to verify the first certificate |
12 | verify return:1 |
13 | --- |
14 | Certificate chain |
15 | 0 s:/C=CN/ST=ZJ/O=JUSENE/OU=OPS/CN=www.jusene.com/emailAddress=admin@jusene.com |
16 | i:/C=CN/ST=ZJ/L=HZ/O=JUSENE/OU=OPS/CN=CA.JUSENE.COM/emailAddress=ADMIN@CA.COM |
17 | --- |
18 | Server certificate |
19 | -----BEGIN CERTIFICATE----- |
20 | MIID5DCCAsygAwIBAgIBATANBgkqhkiG9w0BAQUFADB7MQswCQYDVQQGEwJDTjEL |
21 | MAkGA1UECAwCWkoxCzAJBgNVBAcMAkhaMQ8wDQYDVQQKDAZKVVNFTkUxDDAKBgNV |
22 | BAsMA09QUzEWMBQGA1UEAwwNQ0EuSlVTRU5FLkNPTTEbMBkGCSqGSIb3DQEJARYM |
23 | QURNSU5AQ0EuQ09NMB4XDTE3MDIyNjE4NTMzMloXDTE4MDIyNjE4NTMzMlowczEL |
24 | MAkGA1UEBhMCQ04xCzAJBgNVBAgMAlpKMQ8wDQYDVQQKDAZKVVNFTkUxDDAKBgNV |
25 | BAsMA09QUzEXMBUGA1UEAwwOd3d3Lmp1c2VuZS5jb20xHzAdBgkqhkiG9w0BCQEW |
26 | EGFkbWluQGp1c2VuZS5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIB |
27 | AQDELz7z14ggqKjD4LqBrd9o9O/u8elZwbbbm2uIzUAkDo2idWLAmyke3hDgqS3l |
28 | ZiQZ7uiN78aCjrMW2x6VY2dmVlN9yrAOwlKhXAQg8gLkiZD1UHS2jTgFZ/7EXNCR |
29 | CvXJycN4Vo8zHcQixZkVbkIZE/gQi77O2KyT+fRMoSEn1WXndnwQfBwujQS5Dw2w |
30 | tjRNVBKDCPHHxwf4XJgc+vBEEUjzfYLo7L6EyAF3BQzCH+E4xPTDEemyv3dX5LiM |
31 | oZB0shKPBmb2KGVrIRQc8UxZGVqDQ7sIgqOLx5snmWOHvLagzQ8NgtN8Tz9j4Px6 |
32 | JPBjrlwVgzcmTPp4hdeAS/4HAgMBAAGjezB5MAkGA1UdEwQCMAAwLAYJYIZIAYb4 |
33 | QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmljYXRlMB0GA1UdDgQWBBT8 |
34 | yt7YeRezEhZQ/Seydn+ErvaPZTAfBgNVHSMEGDAWgBT9zWgtLL9xLseRq29gICll |
35 | Km+CiDANBgkqhkiG9w0BAQUFAAOCAQEAR0apSEG/Eo9KRTe+Yje+PJllEnHQlOAk |
36 | XsOS3z1i+mFjWxGzRQXpS7osd+scic9olOq2rlD5TVIvywwHr8soCSN58L7qKIXM |
37 | qSyzilYXbRMw39VuWrwrm1c4O+NiwQX5Nab6XE4hasFuyJhb/usMYFbGUOTQudlg |
38 | UbWYLAPl+jdVNMk/TE+ZPFqounYuqAMDTNuaBV1J6TOxfq7esOxB25B7URT2UDdb |
39 | XGhS1VzPvD9RB6CzhS0Qx/+pDckwoxYgNwJcLJKasIgkB5epVA0zqKknJFuvF2WB |
40 | gedmG4s5FdR3cMXnHVq2r20dOdTRX3kjD75m5VRz/7iwXsOHluBmzA== |
41 | -----END CERTIFICATE----- |
42 | subject=/C=CN/ST=ZJ/O=JUSENE/OU=OPS/CN=www.jusene.com/emailAddress=admin@jusene.com |
43 | issuer=/C=CN/ST=ZJ/L=HZ/O=JUSENE/OU=OPS/CN=CA.JUSENE.COM/emailAddress=ADMIN@CA.COM |
44 | --- |
45 | No client certificate CA names sent |
46 | Server Temp Key: ECDH, prime256v1, 256 bits |
47 | --- |
48 | SSL handshake has read 1691 bytes and written 373 bytes |
49 | --- |
50 | New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384 |
51 | Server public key is 2048 bit |
52 | Secure Renegotiation IS supported |
53 | Compression: NONE |
54 | Expansion: NONE |
55 | SSL-Session: |
56 | Protocol : TLSv1.2 |
57 | Cipher : ECDHE-RSA-AES256-GCM-SHA384 |
58 | Session-ID: 6B53F72925F81A10851DD1D0604B59677DF46DF90E6206C8F08B1B7FF2A2876E |
59 | Session-ID-ctx: |
60 | Master-Key: E582DF702B8EF2748188A282A736BE39F9D24F3F78538C27F2971B452A7B92F5A93E226855F62C5FC05C5AC2F048AE8E |
61 | Key-Arg : None |
62 | Krb5 Principal: None |
63 | PSK identity: None |
64 | PSK identity hint: None |
65 | TLS session ticket lifetime hint: 300 (seconds) |
66 | TLS session ticket: |
67 | 0000 - c7 cb 56 76 a9 ce 25 c2-3c 34 09 e0 64 74 ef c1 ..Vv..%.<4..dt.. |
68 | 0010 - d4 e2 a0 72 df 90 95 8b-71 66 37 7d 16 c1 d3 1f ...r....qf7}.... |
69 | 0020 - 4a 2c 77 fb 86 cc 09 2d-91 95 87 54 a6 7b 3a ac J,w....-...T.{:. |
70 | 0030 - eb 59 b2 6e d6 cb 56 18-88 4c ee b1 dd 23 65 c2 .Y.n..V..L...#e. |
71 | 0040 - 30 24 54 8e b4 6f 93 77-63 bc 39 c3 35 b1 76 65 0$T..o.wc.9.5.ve |
72 | 0050 - 1d d0 2e 2c 86 0c 49 5e-9c 6e 57 d5 72 c1 81 4b ...,..I^.nW.r..K |
73 | 0060 - 67 73 04 ad 6a 70 80 1a-12 a8 3e 69 d5 77 86 b2 gs..jp....>i.w.. |
74 | 0070 - eb b4 f5 7d a7 35 9e 79-11 ac ab 86 58 26 b3 91 ...}.5.y....X&.. |
75 | 0080 - ca c3 94 88 26 9f fb 37-bb ea 62 5f 3c 3d 62 b1 ....&..7..b_<=b. |
76 | 0090 - 4e 2e 37 28 d9 a1 8c 96-2e 42 c6 64 72 7c 30 ae N.7(.....B.dr|0. |
77 | 00a0 - 6b 93 14 54 84 86 74 38-41 4f 52 1e 6b 26 16 59 k..T..t8AOR.k&.Y |
78 | 00b0 - 54 71 b0 1b 86 d3 8e c3-a8 c0 f6 89 16 60 0f ad Tq...........`.. |
79 | |
80 | Start Time: 1490053113 |
81 | Timeout : 300 (sec) |
82 | Verify return code: 21 (unable to verify the first certificate) |
83 | |
84 | 加密会话是在进行的,但是无法验证ca的可靠性,我们需要ca的证书,所以return code 错误码... |
85 | |
86 | 我们把远程的ca自签证书拷贝过来,再来测试下 |
87 | |
88 | CONNECTED(00000003) |
89 | depth=1 C = CN, ST = ZJ, L = HZ, O = JUSENE, OU = OPS, CN = ca.jusene.me, emailAddress = caadmin@jusene.me |
90 | verify return:1 |
91 | depth=0 C = CN, ST = ZJ, O = JUSENE, OU = OPS, CN = www.jusene.com, emailAddress = admin@jusene.com |
92 | verify return:1 |
93 | --- |
94 | Certificate chain |
95 | 0 s:/C=CN/ST=ZJ/O=JUSENE/OU=OPS/CN=www.jusene.com/emailAddress=admin@jusene.com |
96 | i:/C=CN/ST=ZJ/L=HZ/O=JUSENE/OU=OPS/CN=ca.jusene.me/emailAddress=caadmin@jusene.me |
97 | --- |
98 | Server certificate |
99 | -----BEGIN CERTIFICATE----- |
100 | MIID6DCCAtCgAwIBAgIBATANBgkqhkiG9w0BAQUFADB/MQswCQYDVQQGEwJDTjEL |
101 | MAkGA1UECAwCWkoxCzAJBgNVBAcMAkhaMQ8wDQYDVQQKDAZKVVNFTkUxDDAKBgNV |
102 | BAsMA09QUzEVMBMGA1UEAwwMY2EuanVzZW5lLm1lMSAwHgYJKoZIhvcNAQkBFhFj |
103 | YWFkbWluQGp1c2VuZS5tZTAeFw0xNzAzMjAyMjUwMzFaFw0xODAzMjAyMjUwMzFa |
104 | MHMxCzAJBgNVBAYTAkNOMQswCQYDVQQIDAJaSjEPMA0GA1UECgwGSlVTRU5FMQww |
105 | CgYDVQQLDANPUFMxFzAVBgNVBAMMDnd3dy5qdXNlbmUuY29tMR8wHQYJKoZIhvcN |
106 | AQkBFhBhZG1pbkBqdXNlbmUuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIB |
107 | CgKCAQEA5nUfFUWsdM3FP2cl5J5g6AuXT3J/OuzKLwf0FG/tNSgUf5bT+OZ6haPP |
108 | /MXpfc3z/O7SOrUDkQLYsXlH+/PbJX8Z66+EBYrsEN3OEb12uy8lhe+V1FxOoVcA |
109 | SnwoMrt6+5GNINVWgpaLIBhgJyiKds9FPTqMiFkHE6K/7GS/CaShHFAGlLmGC9ZW |
110 | d/LIyO2dAiPSojnQEmKn41DB3of9zNUBpCcwy+3MvIYiKtcKCDPgM2kIaTxhmr1J |
111 | VTi93FhMkoiHRw1nIs6+4ludqZfgLAHmJUecNpx36WUUeTqK/KDiDtJg4haxl29M |
112 | fIbroOfdF6DtYdkuo2H68Sh3D+BZawIDAQABo3sweTAJBgNVHRMEAjAAMCwGCWCG |
113 | SAGG+EIBDQQfFh1PcGVuU1NMIEdlbmVyYXRlZCBDZXJ0aWZpY2F0ZTAdBgNVHQ4E |
114 | FgQULjwjKVzQcGzCCZlfK/pOvzRKNUswHwYDVR0jBBgwFoAUNmgv2nc7L1g2cE/y |
115 | z3CgOhmARlowDQYJKoZIhvcNAQEFBQADggEBAApA1nclL0Bzr6DfinrkzdeLQ/gi |
116 | CX7B1+ePh06L8WTHGrHW0O4vR0MqnvLNWCf9rT2L00FUdSUALEbnOVgTKZ1abxJ7 |
117 | Mnhh2G8yDaFlP0BMWQ/Vwitu9c9gpnES5XC1kCb68BHFPEoiUV/pgWH6Np5dSJwr |
118 | xuh0cLJbBx/V5bkYEa7flYRULdSKFokTdN+wATjRrk4U4z6EGyUvFHqaYbhAyazr |
119 | /R0diJyboMrbjFSim12+ao2FC9RJm2RvVNRlt7hi16X/H+p6ns7xSuaF7LtRC84L |
120 | x4xJ1C4JPxx+/xC7ynhG06MYJqRySIKTlBKmENY7Ym8wh9sS9nczg4Kb4Kc= |
121 | -----END CERTIFICATE----- |
122 | subject=/C=CN/ST=ZJ/O=JUSENE/OU=OPS/CN=www.jusene.com/emailAddress=admin@jusene.com |
123 | issuer=/C=CN/ST=ZJ/L=HZ/O=JUSENE/OU=OPS/CN=ca.jusene.me/emailAddress=caadmin@jusene.me |
124 | --- |
125 | No client certificate CA names sent |
126 | Server Temp Key: ECDH, prime256v1, 256 bits |
127 | --- |
128 | SSL handshake has read 1695 bytes and written 373 bytes |
129 | --- |
130 | New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384 |
131 | Server public key is 2048 bit |
132 | Secure Renegotiation IS supported |
133 | Compression: NONE |
134 | Expansion: NONE |
135 | SSL-Session: |
136 | Protocol : TLSv1.2 |
137 | Cipher : ECDHE-RSA-AES256-GCM-SHA384 |
138 | Session-ID: A82824B6C677BD3ED28124717D2EEE2E9F8324D14EB5A5ACC2255700B24C5BE3 |
139 | Session-ID-ctx: |
140 | Master-Key: CC05274F4C526B0EF32B792C147E1F92F11568C504925DA9C029054F5ECEECADA9D81F849C0A1868D2359B79CF8D4D5B |
141 | Key-Arg : None |
142 | Krb5 Principal: None |
143 | PSK identity: None |
144 | PSK identity hint: None |
145 | TLS session ticket lifetime hint: 300 (seconds) |
146 | TLS session ticket: |
147 | 0000 - ce 28 16 77 04 ed 2f c6-80 6e 01 e2 75 6f f9 be .(.w../..n..uo.. |
148 | 0010 - 3e 67 fa c4 22 b2 92 1e-74 1d c3 de ee d6 01 0d >g.."...t....... |
149 | 0020 - 3b fb 99 dc 7f 29 17 f8-be 11 93 01 ef 81 e1 05 ;....).......... |
150 | 0030 - 8f 28 c1 75 59 89 61 0c-84 74 37 c4 ae a9 d2 15 .(.uY.a..t7..... |
151 | 0040 - 56 98 4b 5e 2f ac f1 6d-76 fa e0 5e 6e 61 29 1c V.K^/..mv..^na). |
152 | 0050 - 1f d5 a5 d4 32 02 61 2e-ac b1 99 cc 23 29 28 38 ....2.a.....#)(8 |
153 | 0060 - 55 53 9c 47 86 67 79 98-52 87 30 99 e0 a5 38 39 US.G.gy.R.0...89 |
154 | 0070 - e7 49 e2 46 46 8f c3 c5-db 78 df 0f c8 f1 c3 87 .I.FF....x...... |
155 | 0080 - ba 56 a2 ee 9f d0 eb 7b-f5 be c0 f1 54 df 72 57 .V.....{....T.rW |
156 | 0090 - 64 48 ba fd 5b ce a9 ec-de 94 7c 50 98 71 8a ec dH..[.....|P.q.. |
157 | 00a0 - d9 bc e3 f7 f5 1c 95 f2-a0 a5 17 a6 d4 2c 14 fd .............,.. |
158 | 00b0 - ab dd c9 c2 85 53 e5 5a-8b d8 6b c5 61 06 00 30 .....S.Z..k.a..0 |
159 | |
160 | Start Time: 1490053371 |
161 | Timeout : 300 (sec) |
162 | Verify return code: 0 (ok) |
163 | --- |
164 | GET /index.html HTTP/1.1 |
165 | HOST:www.jusene.com |
166 | |
167 | HTTP/1.1 200 OK |
168 | Date: Mon, 20 Mar 2017 23:43:14 GMT |
169 | Server: Apache/2.2.15 (CentOS) |
170 | Last-Modified: Mon, 20 Mar 2017 23:41:18 GMT |
171 | ETag: "160129-c-54b3210584d14" |
172 | Accept-Ranges: bytes |
173 | Content-Length: 12 |
174 | Vary: Accept-Encoding |
175 | Connection: close |
176 | Content-Type: text/html; charset=UTF-8 |
177 | |
178 | hello https |
179 | closed |
ok,测试成功,如需要在浏览器也能正常使用ssl会话,而不是出现会话不可信的提示,我们就需要把ca的证书导入到浏览器的证书管理中。
前不久谷歌浏览器和火狐等主流浏览器已经对非https的网站标为非安全的网站,所以全网https的时代也已经不远了。
httpd自带的工具程序
htpasswd: basic认证基于文件实现时,用到的账号密码文件生成工具
apachectl:httpd自带的服务控制脚本,支持start和stop
apxs:由httpd-devel包提供,扩展httpd使用第三方模块的工具
rotatelog: 日志滚动工具
suexec: 访问某些有特殊权限的资源时,临时切换至指定用户身份运行
ab: apache bench
httpd的压力测试
压力测试工具有很多,如:
ab,webbench,http_load,seige
jmeter,loadrunner
tcpcopy:网易,复制生产环境的真实请求,并将之保存下来
ab测试是httpd自带的压力测试工具:
ab [OPOTION] URL
- -n: 总请求量
- -c:模拟的并发数
- -k: 以持久连接模式测试